Volatility Forensics Basics
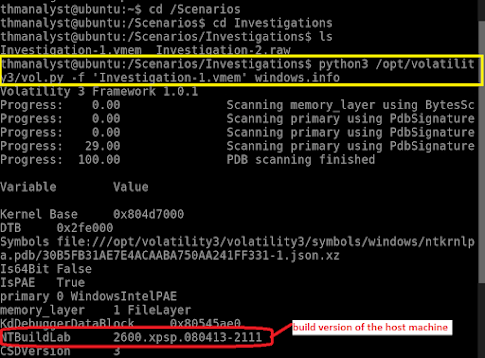
How to find build version of the host machine via Forensic Image analysis of Volatility
Navigate to the path where image file is present then
type /Directory/Path python3 /opt/volatility3/vol.py -f 'FILENAME' windows.info
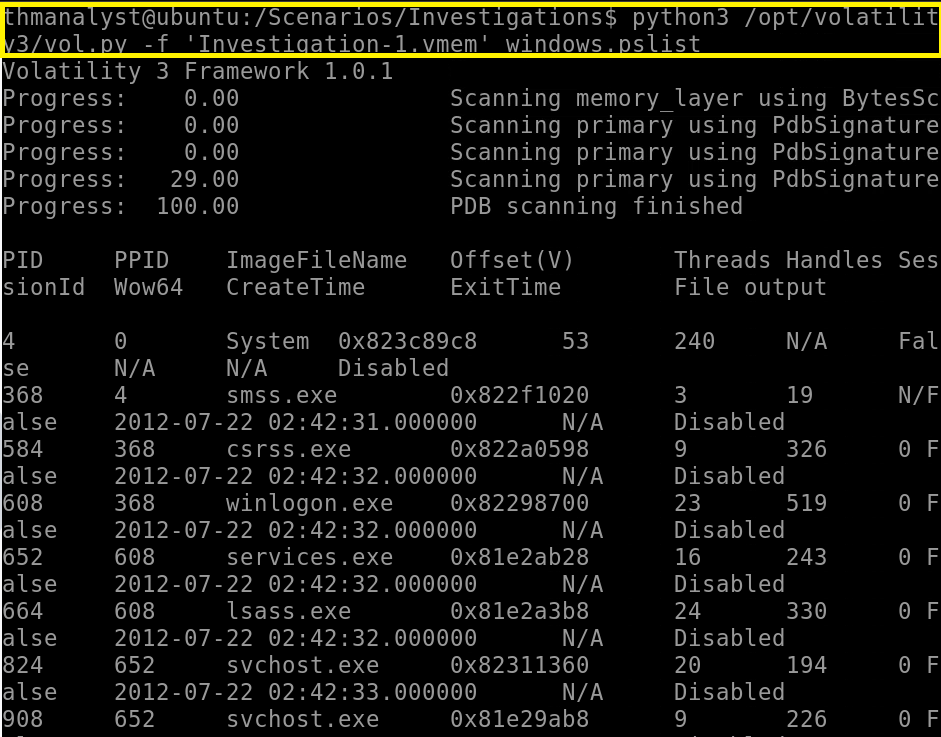
To Find all processes associated including suspicious and legit ones,
python3 /opt/volatility3/vol.py -f 'Filename' windows.pslist
This process seems to be a malicious one
python3 /opt/volatility3/vol.py -f 'FILENAME' windows.pstree
To Check associated artifacts such as browser user's agent we perform dump asgainst the parent process id it writes entire dump on /tmp directory
python3 /opt/volatility3/vol.py -f 'Investigation-1.vmem' -o /tmp/ windows.memmap.Memmap
--pid 1484 --dump
To check for keywords in strings use the following command
strings /tmp/*.dmp | grep -i "user-agent"



Comments
Post a Comment